Clash of clan
1. Provide an overview of the game, the logistics, strategies used, and your experience.
Clash of Clans is a popular iPad/iPhone/iPod/Android game created by "Supercell". It has been available internationally on the iTunes store for free since its initial v1.7 release on 2 August 2012, and on the Google Play Store since 8 October 2013. Clash of Clans is a strategy game where players can construct and expand one's village, unlock successively more powerful warriors and defenses, raid and pillage resources from other villages, create and join Clans and much, much more.Although Clash of Clans is Free-to-Play, additional in-game currency can be purchased for real money from the Apple App Store/Google Play Store in the form of In-App Purchases. However, all features of the game are open to players who choose not to make In-App Purchases. Clash of Clans is available on iOS and Android devices!
(Clash of clans wiki,2015)
http://clashofclans.wikia.com/wiki/Clash_of_Clans_Wiki
2. Address the collaborative process within the clan you joined (this means you will use each part of the process, discuss the section and provide examples from your experience).
Clans are groups of players that join together in order to compete with other Clans in two ways: the first is to pool their trophies and battle to collect the most trophies, and the second is to win Clan Wars for loot and prestige. Members of Clans have a private chat for socializing with each other and are able to donate troops to each other. Within a Clan there are four ranks, member, elder, co-leader, and leader. Including the leader, you can have up to 50 members in a Clan.
Joining a Clan
To be a member of a Clan you must first repair your Clan Castle. To do this will cost you 10,000 gold. Once your Clan Castle has been repaired you have the option of joining or creating a Clan. There are various ways to join a Clan. Below are some examples:
View a Clan that has the status 'Anyone Can Join' and tap the 'join' button.
Send a request to join a Clan that has the status 'invite only'.
Go on global chat and watch for people recruiting members to join their Clan.
Accepting an invitation sent by a clan elder/co-leader/leader.
Note: Some Clans have a minimum trophy requirement to join their Clan; you cannot join nor send a request to join if you do not meet the trophy requirement (you can, however, be invited and accept the invite). The trophy requirement is set by the Clan leader or co-leader and can vary from from 0 to 4,200.
Clan Ranks
(Not to be confused with Clan Rankings)
Leader
Clan leaders are the ones who have the big responsibility of managing their Clan. In order to create a brand-new Clan, it costs an additional 40,000 gold, whereupon the player will immediately become the first member and leader of the new Clan. The leader has the administrative authority to invite players to join their Clan, accept or decline requests to join, start wars, and promote/demote members to and from eldership and/or co-leader. The leader can kick out co-leaders, elders, and members.
Additionally, a Clan leader has the ability to demote themselves and promote another player to leader. This move is generally only made in particular circumstances and should be exercised with extreme caution, as once another member is made leader the former leader no longer holds the same administrative powers. Typically a Clan leader should only do this if the person they promoted was entirely trusted. If the Clan leader leaves without promoting someone else to leader, the co-leader who has been in the clan for longest will automatically become leader. If there are no co-leaders, the most senior elder will take the position, and if there are no co-leaders nor elders the oldest member in the Clan will obtain leadership. If the leader is the only one in the Clan when he leaves, the Clan will close.
The main difference between the Clan leader and an co-leader is that only the leader has the authority to bestow (and withdraw) the title of co-leader on another player. It is strongly discouraged for leaders to freely give away leader status, as this will completely and irrevocably relinquish control to the new leader. There can only be one leader at a time.
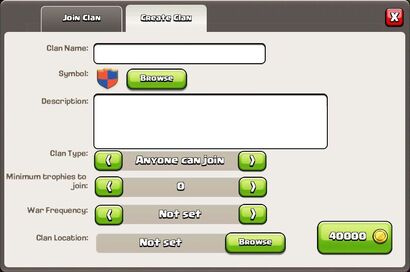
Making a new Clan
Assuming his or her
Clan Castle is already rebuilt, a player must do the following to create a new Clan:
- Choose the badge and name of the clan.
- Make a description of your clan to let know others what you're all about (optional)!
- Select the status of the clan/clan type. i.e.; Anyone can join, invite only or closed.
- Set the amount of trophies required to join the clan (this field can be left blank and the default will be 0).
- Select the war frequency of the clan.
- Choose out the Clan Location of your clan.
- Pay the required 40,000 gold.
Editing Your Clan
The leader or co-leader(s) of the Clan may edit the
badge, Clan type, minimum
trophyrequirement and description of the Clan. It is not possible to change the name of a Clan once it has been created.
Clan setting updates can now be seen in the Clan Chat, indicating who changed them.
Clan Types
Closed
You are not allowed to join the Clan at this time, even if there is room and you fit the requirements. However, you can be part of a closed Clan if invited personally by an elder/co-leader or the leader of the said Clan, invitations can also bypass Trophy requirements set by the Clan.
Invite Only
You can apply to join this Clan if you have at least the minimum number of
trophies required. Your message will pop up in the Clan chat, at which time a
clan elder,
co-leader or a
leader can accept you (which causes you to immediately join the Clan) or reject you. If you have been rejected you will have to wait 6–8 hours until you can apply again for the same Clan. You will receive a message if you are rejected.
Members cannot invite or accept pending invites. You can accept or decline an invite sent by the
elder,
co-leader or
leader of a clan.
Note that you can apply to multiple Clans at once. You will join the first Clan that accepts your application, and any subsequent Clans that try to accept you will receive a message that you are already in another Clan (although the application will stay in chat until it is either accepted or rejected, and there is otherwise no indication that you have joined another Clan in the meantime).
Anyone Can Join
This is a type of Clan where anyone can join. Even if anyone is able to join, you must still have at least the minimum number of
trophies that the Clan requires.
Minimum Trophy Requirement
This may be adjusted from 0-4,200. It will stop players of a lower
trophy count from joining, but will hopefully attract higher levels. A player of a lower
trophy count may join if invited by an elder, co-leader or leader of the clan. The minimum
trophy requirement can be increased by increments of 200 from 0 to 1,000, and by increments of 100 from 1,000 to 4,200. Anyone without the required amount of
trophies cannot join the Clan, but Clan members or elders which are below the
trophy requirement will not be automatically kicked from the Clan (the leader or co-leaders can manually do so, of course). An elder cannot kick an elder, nor can a co-leader kick a co-leader.
Clan Badge
All Clans have a badge, which is initially designed by the leader when he or she creates the Clan. The leader can customize the badge using the 79 preset patterns, 12 colors and 20 borders that Supercell has provided.
(http://clashofclans.wikia.com/wiki/Clans,2015)
3. Present the type of communication used, examples of inappropriate communication as well as inappropriate behaviour.
Type of communication used
The Internet and E-mail
This was made for conveying over systems. The most well-known correspondence is email, in light of the fact that it is utilized for both business and individual correspondence
Voice over Internet Protocol (VoIP)
This sort of correspondence permits individuals to see one another whilst talking. This kind of correspondence empowers the non-verbal communication, in light of the fact that they are synchronously utilizing the Internet
Social networking
The design is to share what is going ahead in your life. Instagram is a stage of sharing your photographs
Examples of Inappropriate Communication
Accepting assembles or messaging in a conference or class
Gushing wrong material out in the open
Chatting on the telephone amid feast times
Utilizing institutional PCs for non-institutional purposes (e.g. work PCs for individual or school PCs for non-scholarly purposes)
Utilizing organization telephones for individual utilization
Wrong utilization of work resources
Examples of inappropriate behaviour
irritating or culpable or debilitating conduct towards an individual or gathering I the work environment
work environment savagery
hindrance in the working environment by liquor or different substances
4. Address the issue of how, if at all, this game could be used to educate the younger generation about digital citizenship.
the diversion is in view of the advanced citizenship manual aide, so the learners and more individuals will pick up learning on computerized citizenship and how it influences our every day lives
(Anon (a), (2013). MIT Technology in Review. [Internet] 2013: The Year of the Internet of Things. Available from: http://www.technologyreview.com/view/509546/2013-the-yearof-the-internet-of-things/)
5. Research needs to be referenced and substantiate your arguments (Please use at least five (5) relevant and authentic sources).
Why do you need to reference?
There are many reasons why referencing is important, go to the Home page and check out the view points given in the short videos or check out the ideas listed below.
To distinguish your own ideas from those of someone else.
To cite different points of view.
To validate what you are writing, by referring to documented evidence. Published work for instance can be used to support your argument and add credibility to your writing.
To inform readers of the scope and depth of your reading.
To integrate information by assessing, comparing, contrasting or evaluating it, to show understanding.
To emphasise a position that you agree or disagree with.
To refer to other research that leads up to your study.
To highlight a pertinent point by quoting the original.
To enable readers to consult the original source independently. For instance the interpretation you give may be different from the one intended.
(Referencite,2015)
(Palgrave,2015)
(Skillsyouneed,2015)
(Universityofreferencing,2015)
(sokogskriv,2015)